ASP.NET Core: Creating Resilient Microservices
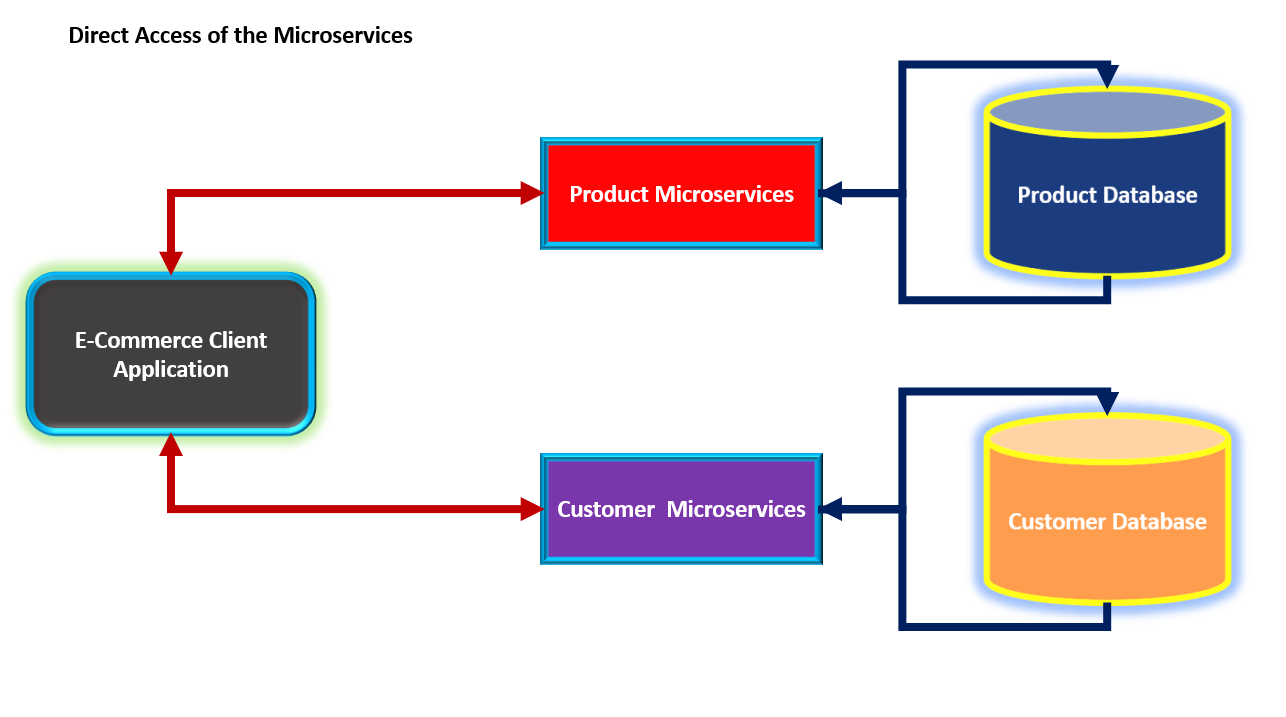
In this article, we will see how to implement resilient Microservices using ASP.NET Core. The question here is why we need to implement such a design for the Microservices? Consider, the design for Microservices shown in Figure 1 Figure 1: The Direct Access of Microservices from the client application As shown in Figure 1, the E-Commerce client application directly accesses Product and Customer Microservices. The client application will be able to receive data from these services successfully if the Product and the Customer services are up and running. But in case one of these services is down because of some errors, then the client application will not get the data and hence might be a reason to crash the client app. In this case, although the client app is not responsible for the stability of the Microservices still any issue that occurs in Microservices will crash the client application. The question here is, how to resolve such kind of a design flow in our applicat...
